Soren
New member
Overview
In today's digital world, Internet restrictions and IP bans have become a real challenge that many users have to face. Whether you are an occasional social media user or a professional who needs to access information frequently, there are seemingly invisible but real barriers to accessing the Internet. The reasons behind these restrictions are complex and varied, and may be due to content censorship requirements or a company's desire to manage its employees' online behaviour.
These restrictions are usually implemented through technical means such as firewalls, deep packet inspection, etc. and are designed to control or prevent users from accessing specific content. While these restrictions are often hidden in the background, their impact on our web experience is obvious. Understanding how these technologies work can not only help us better deal with these challenges, but also make us more comfortable in the face of these obstacles. So how do these limitations affect our daily lives? Let's find out together through this article!
What is Internet Restriction? Why is it Internet restricted?
Internet restrictions in their common form
Imagine you are surfing the Internet and find yourself unable to access certain popular websites or the pages load unusually slowly, this is actually Internet Restrictions at work. Simply put, Internet restrictions are technical means or policy regulations that limit or prevent you from accessing certain online content or services. This kind of restriction can take many forms. For example, the government may block some news websites or social media platforms, which is known as content censorship; a company may restrict its employees from accessing certain recreational websites during working hours, which is known as access control. Then there is the more extreme case of completely cutting off internet access to a region or country, resulting in all users being unable to connect to the internet. In a nutshell, Internet restrictions are designed to control the flow of information or manage users' online behaviour.
How IP Blocking Works
Have you ever been "banned" from a website because you did something inappropriate on the Internet, and never been able to return? That's where IP bans come into play. Every computer or mobile phone has a unique address when you access the Internet, which is like your Internet ID. When you visit a website, this address is recorded. If this address is blacklisted for some reason, then you are banned from visiting the site again. This means of blocking is very straightforward and can be temporary or permanent, and is mainly used to stop violations or to ban users from certain areas in order to comply with specific legal requirements.
Common restrictions

So how do they do all this blocking? There is actually a whole set of technical tools at work behind the scenes. Firewallsare the most basic line of defence, they are like the gatekeepers of the online world, blocking connections that don't conform to the rules by monitoring and controlling the traffic coming in and out of the network. And a little more advanced technology is Deep Packet Inspection (DPI), which not only looks at what requests you send, but also scrutinises the content of the data you transmit, and if it finds something non-compliant, it immediately blocks it. There's also a common technology called a content filtering system, which automatically identifies and blocks specific keywords, images, or file types so that you can't access that restricted content. These technologies usually work in tandem to make Internet restrictions more comprehensive and precise.
Internet restrictions have long been a part of our online presence, and many times you may not even realise they exist. While they can limit your freedom of access, if you understand how they work, you can deal with these challenges more comfortably. Faced with these invisible barriers, how should we get around these restrictions?
How to Effectively Bypass Internet Restrictions
1. Clearing browser cache and cookies
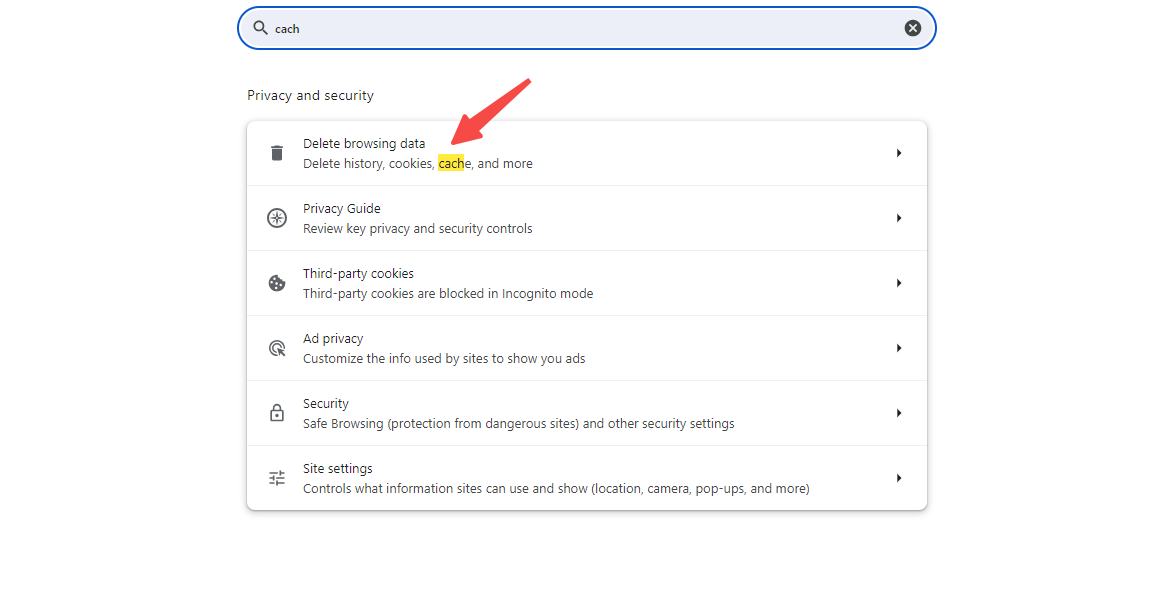
Sometimes websites restrict your access by using browser caches and cookies to track your visit history and behaviour. By clearing these caches and cookies, you can "reset" your browser's access status so that the website thinks you are a new visitor, which can sometimes bypass some of the basic restrictions.
However, this method has its limitations. If a website takes more stringent measures, such as logging your behaviour on the server side or using more sophisticated tracking techniques, simply clearing your cache and cookies may not work, and may even lead to more stringent restrictions, such as outright blocking of your IP. in this case, clearing your cache and cookies will not solve all the problems, and will need to be combined with other methods to bypass the restrictions more efficiently .
2. Use of different browsers or devices

If you are experiencing limitations when using one browser or device, it may be a good solution to try switching to another. Different browsers handle website data differently, so switching browsers may allow you to bypass certain restrictions. Using a new device, on the other hand, can bypass the restrictions associated with a particular device and allow you to regain access.
However, it is important to note that while this IP bypass strategy may be effective, if the restriction is based on your account information or IP, this switch may not completely solve the problem. In this case, additional measures may be required to counter the tighter restrictions.
3. Use of Residential Proxies

Using Residential Proxies is a very effective way to bypass Internet restrictions. Residential Proxies use the Internet address assigned to a normal home, rather than the address of a data centre, which makes you look like a normal home user, rather than a user accessing through Proxies.
Because these addresses are closer to the real user's visit, it is more difficult for websites to recognise and block them. This means that using Residential Proxies makes it easier to bypass restrictions, especially when faced with tighter restrictions.
Residential Proxies not only help you access restricted content without problems, but also provide greater anonymity and security, reducing the risk of being tracked or blocked. The flexibility and reliability of such Proxies makes it a powerful tool for dealing with network restrictions. Whether you are using Proxies for work or personal entertainment, Residential Proxies provide a more stable and stealthy way to access the Internet, ensuring that your online experience is unhindered.
How to Bypass Restrictions Using Residential Proxies
Step 1: Registration and Login
Firstly, you need to have a Residential Proxies, you can choose the right Residential Proxies, here we recommend to use PROXY.CC, secondly, you can register a Residential Proxies account. You can refer to the registration document or directly use your Google account to login. Once you have registered, enter your account and click on "My Account" under your username in the top right corner of the homepage, this will take you to the "Instruction Panel" screen. This will take you to the "signup board" screen where you can select and purchase the Proxies that are right for you. New users can also sign up for free by contacting customer service.
Step 2: Configure Antidetect Browser
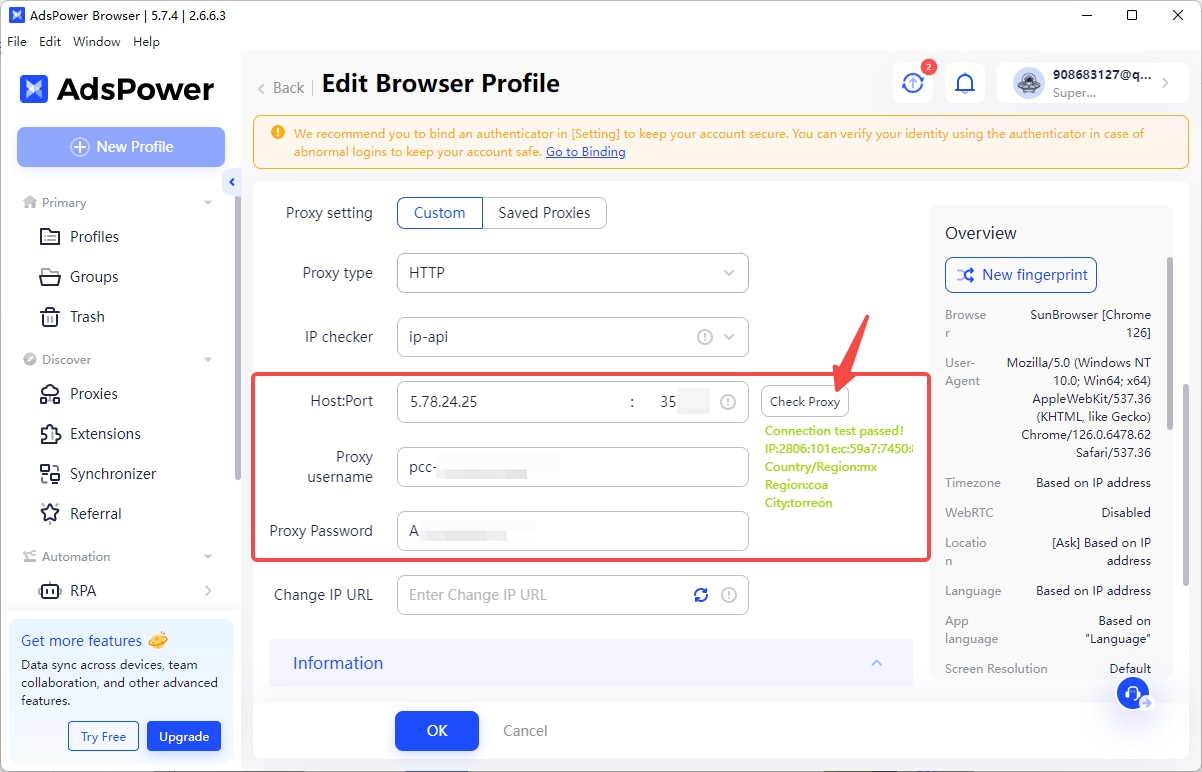
There are many suitable Antidetect Browser in the market, here I use Ads Antidetect Browser as an example. Firstly, download and install AdsPower Antidetect Browser, register and login, then click "New Browser" in the upper left corner. In "Proxies Type", select HTTP, and in "IP Query Channel", select ip-api, then enter the proxy information you copied in the "Host ort" field. Then, click Check Proxies and make sure the Proxy Service's IP address is displayed in the detection screen to create the Porfiles successfully.
ort" field. Then, click Check Proxies and make sure the Proxy Service's IP address is displayed in the detection screen to create the Porfiles successfully.
Detailed instructions: How to set up Proxies with AdsPower Browser
Once created successfully, open the Antidetect Browser window and you'll be able to access it with the configured Proxies. No more suffering from geolocation restrictions.
In today's digital world, Internet restrictions and IP bans have become a real challenge that many users have to face. Whether you are an occasional social media user or a professional who needs to access information frequently, there are seemingly invisible but real barriers to accessing the Internet. The reasons behind these restrictions are complex and varied, and may be due to content censorship requirements or a company's desire to manage its employees' online behaviour.
These restrictions are usually implemented through technical means such as firewalls, deep packet inspection, etc. and are designed to control or prevent users from accessing specific content. While these restrictions are often hidden in the background, their impact on our web experience is obvious. Understanding how these technologies work can not only help us better deal with these challenges, but also make us more comfortable in the face of these obstacles. So how do these limitations affect our daily lives? Let's find out together through this article!
What is Internet Restriction? Why is it Internet restricted?
Internet restrictions in their common form
Imagine you are surfing the Internet and find yourself unable to access certain popular websites or the pages load unusually slowly, this is actually Internet Restrictions at work. Simply put, Internet restrictions are technical means or policy regulations that limit or prevent you from accessing certain online content or services. This kind of restriction can take many forms. For example, the government may block some news websites or social media platforms, which is known as content censorship; a company may restrict its employees from accessing certain recreational websites during working hours, which is known as access control. Then there is the more extreme case of completely cutting off internet access to a region or country, resulting in all users being unable to connect to the internet. In a nutshell, Internet restrictions are designed to control the flow of information or manage users' online behaviour.

How IP Blocking Works
Have you ever been "banned" from a website because you did something inappropriate on the Internet, and never been able to return? That's where IP bans come into play. Every computer or mobile phone has a unique address when you access the Internet, which is like your Internet ID. When you visit a website, this address is recorded. If this address is blacklisted for some reason, then you are banned from visiting the site again. This means of blocking is very straightforward and can be temporary or permanent, and is mainly used to stop violations or to ban users from certain areas in order to comply with specific legal requirements.
Common restrictions

So how do they do all this blocking? There is actually a whole set of technical tools at work behind the scenes. Firewallsare the most basic line of defence, they are like the gatekeepers of the online world, blocking connections that don't conform to the rules by monitoring and controlling the traffic coming in and out of the network. And a little more advanced technology is Deep Packet Inspection (DPI), which not only looks at what requests you send, but also scrutinises the content of the data you transmit, and if it finds something non-compliant, it immediately blocks it. There's also a common technology called a content filtering system, which automatically identifies and blocks specific keywords, images, or file types so that you can't access that restricted content. These technologies usually work in tandem to make Internet restrictions more comprehensive and precise.
Internet restrictions have long been a part of our online presence, and many times you may not even realise they exist. While they can limit your freedom of access, if you understand how they work, you can deal with these challenges more comfortably. Faced with these invisible barriers, how should we get around these restrictions?
How to Effectively Bypass Internet Restrictions
1. Clearing browser cache and cookies

Sometimes websites restrict your access by using browser caches and cookies to track your visit history and behaviour. By clearing these caches and cookies, you can "reset" your browser's access status so that the website thinks you are a new visitor, which can sometimes bypass some of the basic restrictions.
However, this method has its limitations. If a website takes more stringent measures, such as logging your behaviour on the server side or using more sophisticated tracking techniques, simply clearing your cache and cookies may not work, and may even lead to more stringent restrictions, such as outright blocking of your IP. in this case, clearing your cache and cookies will not solve all the problems, and will need to be combined with other methods to bypass the restrictions more efficiently .
2. Use of different browsers or devices

If you are experiencing limitations when using one browser or device, it may be a good solution to try switching to another. Different browsers handle website data differently, so switching browsers may allow you to bypass certain restrictions. Using a new device, on the other hand, can bypass the restrictions associated with a particular device and allow you to regain access.
However, it is important to note that while this IP bypass strategy may be effective, if the restriction is based on your account information or IP, this switch may not completely solve the problem. In this case, additional measures may be required to counter the tighter restrictions.
3. Use of Residential Proxies

Using Residential Proxies is a very effective way to bypass Internet restrictions. Residential Proxies use the Internet address assigned to a normal home, rather than the address of a data centre, which makes you look like a normal home user, rather than a user accessing through Proxies.
Because these addresses are closer to the real user's visit, it is more difficult for websites to recognise and block them. This means that using Residential Proxies makes it easier to bypass restrictions, especially when faced with tighter restrictions.
Residential Proxies not only help you access restricted content without problems, but also provide greater anonymity and security, reducing the risk of being tracked or blocked. The flexibility and reliability of such Proxies makes it a powerful tool for dealing with network restrictions. Whether you are using Proxies for work or personal entertainment, Residential Proxies provide a more stable and stealthy way to access the Internet, ensuring that your online experience is unhindered.
How to Bypass Restrictions Using Residential Proxies

Step 1: Registration and Login
Firstly, you need to have a Residential Proxies, you can choose the right Residential Proxies, here we recommend to use PROXY.CC, secondly, you can register a Residential Proxies account. You can refer to the registration document or directly use your Google account to login. Once you have registered, enter your account and click on "My Account" under your username in the top right corner of the homepage, this will take you to the "Instruction Panel" screen. This will take you to the "signup board" screen where you can select and purchase the Proxies that are right for you. New users can also sign up for free by contacting customer service.
Step 2: Configure Antidetect Browser
There are many suitable Antidetect Browser in the market, here I use Ads Antidetect Browser as an example. Firstly, download and install AdsPower Antidetect Browser, register and login, then click "New Browser" in the upper left corner. In "Proxies Type", select HTTP, and in "IP Query Channel", select ip-api, then enter the proxy information you copied in the "Host

Detailed instructions: How to set up Proxies with AdsPower Browser
Once created successfully, open the Antidetect Browser window and you'll be able to access it with the configured Proxies. No more suffering from geolocation restrictions.